iShare In The Cloud Connectivity
Overview
iShare In The Cloud is a cost effective, fully managed service provided by Astun Technology on behalf of our customers.
- Customers no longer need to procure servers, set up operating systems or be dependent on data centre space, power and server support staff to run their Enterprise GI platform.
- Core iShare upgrades, server management and security are managed by our team of cloud experts.
- Disaster recovery is managed within the cloud environment ensuring that the solution is available in multiple availability zones within the EU.
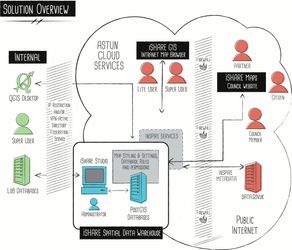
When deploying to the cloud, connectivity back to your Network estate needs to be considered especially with regards to the security requirements and also the user management and authorisation methods.
Network Connectivity
iShare In the Cloud is deployed in your own Virtual Private Cloud ensuring that each Astun customer has their own isolated section of of the Astun Cloud Services. Subnets can then be created within these to allow a public facing environment to have web connectivity whilst having your internal data and applications kept within a private sub net which is connected to the On-Premise customer network estate. Different Network Connectivity options are as follows:
| Type | Description | Pros | Cons |
|---|---|---|---|
| Virtual Private Network | A virtual private network (VPN) is a technology that creates an encrypted connection over a less secure network - in this case the network being the Internet between the Customer Network and the Virtual Private cloud. The benefit of using a VPN is that it ensures the appropriate level of security to the connected systems when the underlying network infrastructure alone cannot provide it. Search the following page for Q. What customer gateway devices are known to work with Amazon VPC? |
|
|
| Restrict Access by IP address | Restricting Access by IP address is a mechanism that ensures that the only requests that originate from the customer Network Estate are permitted. As the communications are occurring over the Internet there would be minimal risk that a Man-in-the-middle attack could occur but this is extremely rare. If secure protocols are used this adds extra security i.e. https, ftps / sftp etc The following page gives technical details of how this is configured - suitable reading for Network Engineers. |
|
|
| Open Internet | No restriction on where a request originates from and no data is encrypted whilst in transit. This is the least secure and could be prone to Denial of Service attacks etc. As with the Restrict Access by IP address above secure protocols can also be used i.e. https, sftp / ftps |
|
|
In addition to the consideration of Network Connectivity, iShare in the Cloud, requires a mechanism by which it can distinguish between different users so that it can identify what profiles to apply to those users when accessing iShare GIS.
Type | Description | Pros | Cons |
|---|---|---|---|
| Azure AD SSO | With Azure AD SSO (Single Sign On) you can login to iShare using the same user account as your Azure Active Directory. |
|
|
Active Directory Federated Services (ADFS) | iShare In The Cloud can be fully integrated within a corporate Microsoft Active Directory domain via ADFS (the same method that Microsoft use with Office 365) ensuring internal security compliance. Therefore iShare In The cloud securely connected to the corporate network via a VPN (if required) via the most viable network location end point ensuring that remote workers have maximum bandwidth when securely connected to the network estate. |
|
|
| Manually created users | Manual creation and management of local users is performed using standard Windows Server tools which combined with Windows Groups allows for fine grained security controls, similar to Enterprise Domain configurations. This is ideal, and has been implemented for scenarios where:
Account creation and / or Password management can become an issue without Third Party tools. |
|
|
Third Party software Management solutions | Normally combined with either Virtual Private Network or Restrict Access by IP address connectivity options. Two options are:
|
|
|
| Anonymous access | Anonymous access has no Authorization of individual users. Some functionality of iShare GIS wouldn't be available including Annotations and Feature Editing. Note For any Internal instance, this would NOT be implemented by Astun Technology unless either the Virtual Private Network or Restrict Access by IP Address were implemented. |
|
|