| Page Properties | ||||||
|---|---|---|---|---|---|---|
| ||||||
|
...
| Step | Notes | ||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|
Step 1 - Check iShare GIS config | Before starting, check that:
| ||||||||||
| Step 2 - Install the Windows Identity Framework and SDK | The Windows Identity Framework is required by iShare for the token exchange. The SDK includes the Federation Utility Wizard used in Step 4. Both therefore need to be installed.
| ||||||||||
| Step 3 - Configure IIS |
| ||||||||||
| Step 4 - Certificate installation |
Most often self-issued certificates are used but sometimes they must be imported from ADFS, if so:
| ||||||||||
| Step 5 - Run the Federation Utility Wizard | Start the wizard The Federation Utility Wizard ( Run the Federation Utility Wizard as an Administrator. This is most important as it allows a scheduled task to keep the federation metadata documents up to date. | ||||||||||
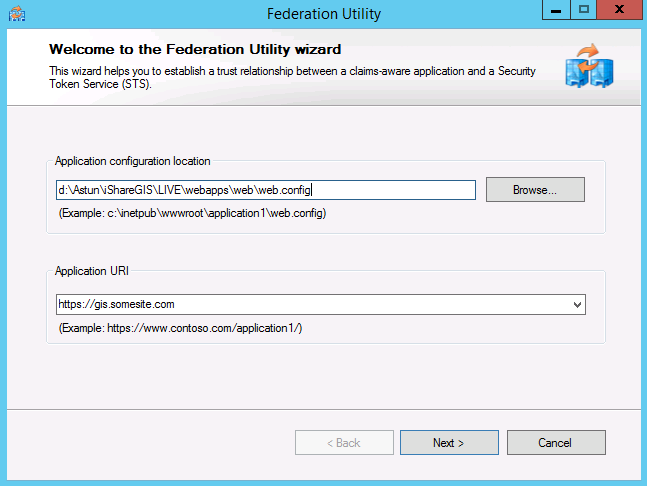
Screen 1 - Welcome Enter the application configuration location (the web.config) and the Application URI (https://gis.somesite.com) | |||||||||||
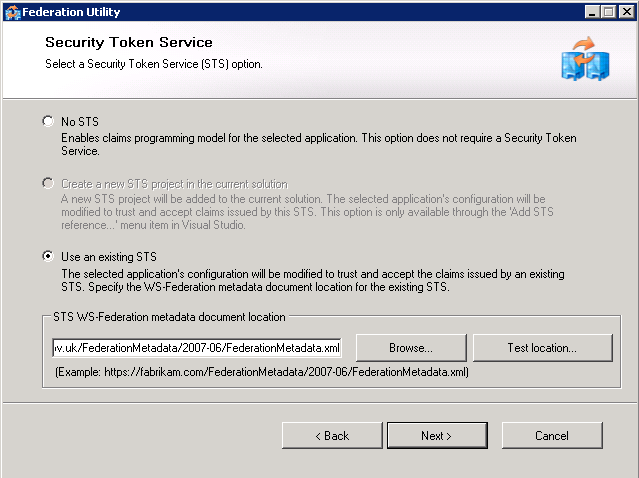
Screen 2 - Security Token Service From Stage 2, the customer should provide us with the URL of a FederationMetadata.xml file, enter that in STS WS-Federation metadata document location. The URL will follow this structure: https://<FQDN>/federationmetadata/2007-06/federationmetadata.xml. NOTE: In some circumstances the customer does not make their ADFS proxy available to us, in that situation they must download the file themselves and send it to us, save it to the {{WebApps}} folder for the iShare GIS installation and then enter the document's local path in here instead of a URL. Always click Test location... this will ensure that the file can be reached. | |||||||||||
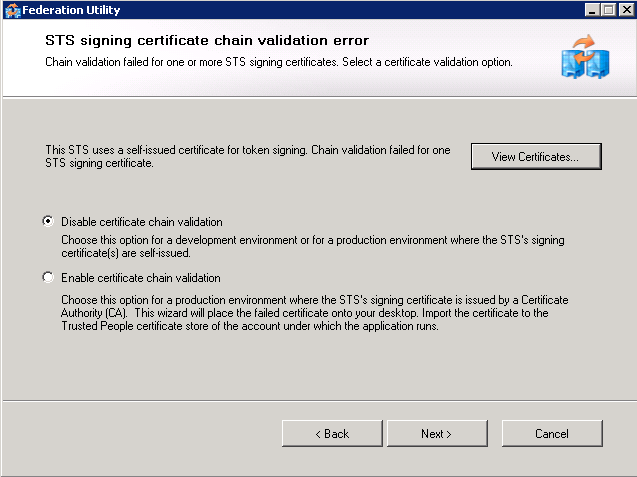
Screen 3 - STS signing certificate chain validation error
This screen will appear if the certificate chain cannot be validated all the way back to the root Certificate Authority (CA). This will happen if the certificate was self-issued or if the CA is not one trusted by the server (e.g. an Active Directory CA when the iShare server is not part of the Active Directory). At this point there are three choices:
| |||||||||||
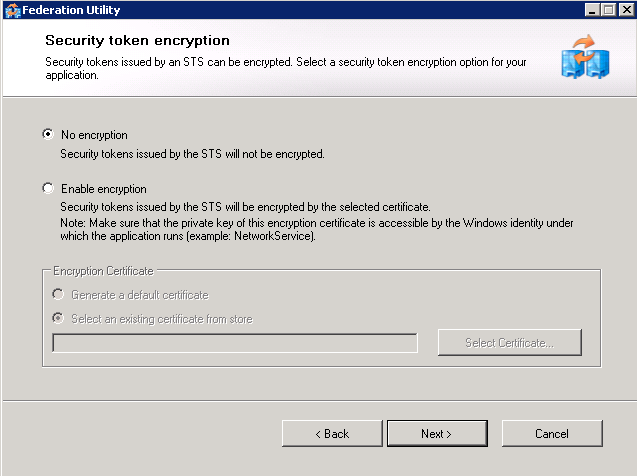
Screen 4 If encryption was chosen in the ADFS Relying Party configuration then enable encryption. If they have provided the private key of the token encryption certificate it should be selected here. After the Federation Utility has been completed allow the iShare GIS web application pool access to the certificate through MMC's Certificates snap-in. | |||||||||||
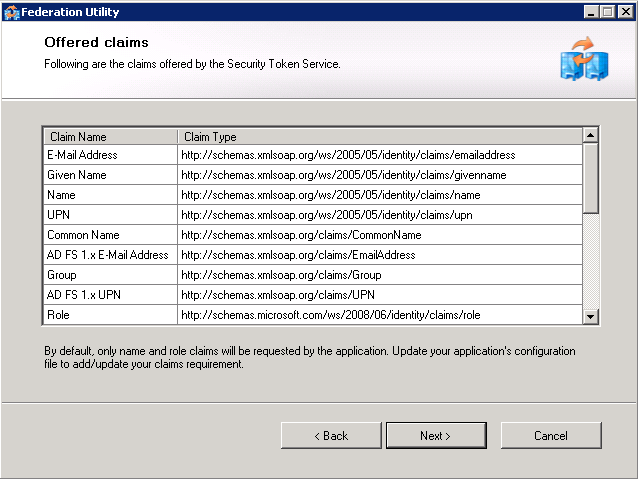
Screen 5 - Offered clains The utility now presents a series of claims offered by the Security Token Service. All look good? Click next. | |||||||||||
Screen 6 - Scheduled task Select scheduled task. This is only effective if the STS federation metadata document (see Screen 2) has been supplied via URL. This is most important as otherwise the trust will eventually break down when certificates expire. Copy the configuration summary to the iShare GIS module page in the client notes. | |||||||||||
Additional Tasks Check Windows Task Scheduler for the WIF task. This will be under Task Scheduler Library > Microsoft > Windows > WindowsIdentityFoundation. You may wish to run this to see if it completes correctly. Did you specify a certificate for security token encryption? If so you will have to allow the iShare GIS web application pool read access to the certificate. Do this by running MMC > Local Computer > Certificates snap-in > Select certificate > Right click Manage Private Keys. Add application pool user account. If required, add logging to the web.config file for the web application - this can be done by adding the following top-level element to the XML, at the end of the file:
The generated log will show details of users and claims. Note that this log can grow very large, so the code above should be disabled when not needed. |
...